Manchester, UK - 7th + 8th May, stand A39
The most advanced Adversary in The Middle feed available
Block AiTM attacks before they even start
Sign up to be kept up to date with adversary intel:
Empower Microsoft Defender
Seamlessly import our indicators into Microsoft Defender and benefit from real time, constantly updated, protection for all of your users.
Block access to AiTM infrastructure
to
Alert and Notify
Take advantage of Defenders blocking and alerting functionality to block user access to and alert your security team when AiTM arises.
Protect your users, notify your security team
Real time blocking via conditional access policies
Subscribe to our named location feed and seamlessly ingest our data, in real time, into your conditional access policies - ensuring AiTM infrastructure is unable to authenticate to your environment even if your users are hit.
Block access from AiTM infrastructure
from
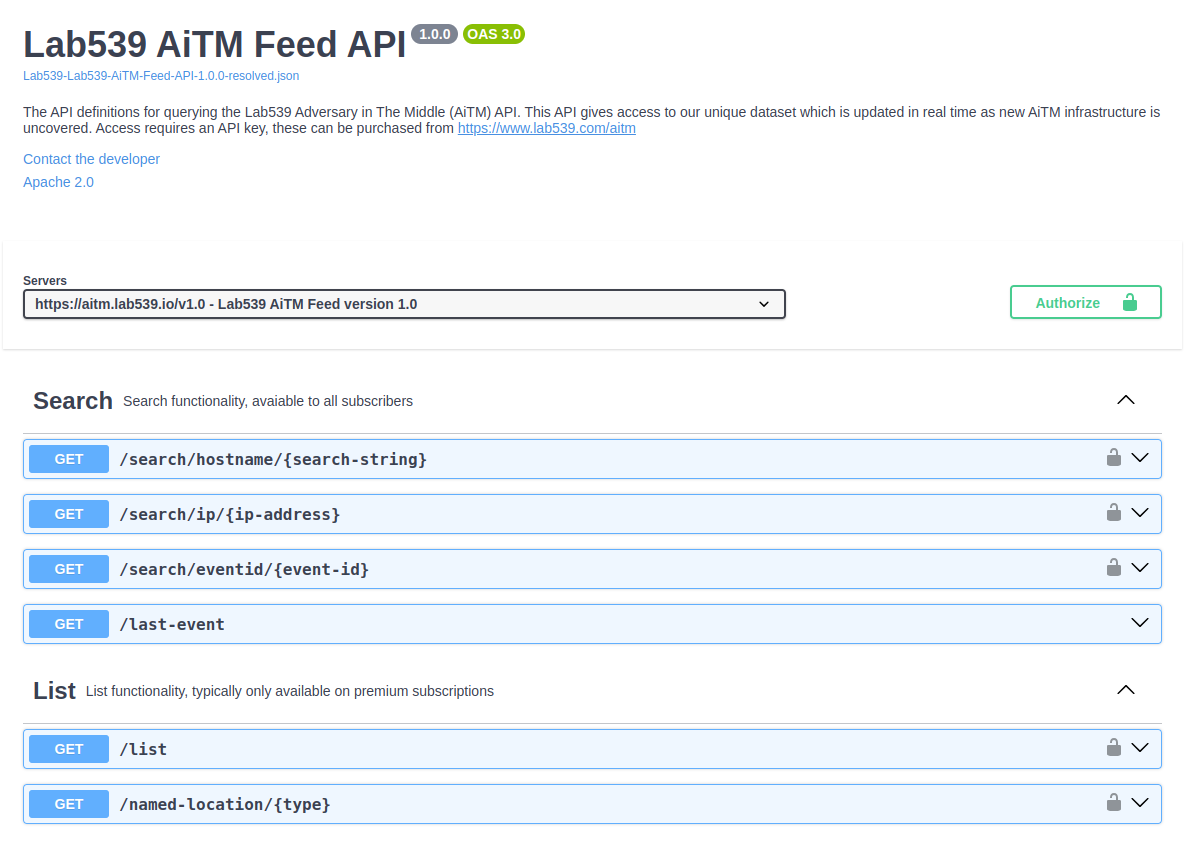
Take advantage of the API to enable immense flexibility
Take advantage of our API in order to achieve unlimited integrations with whatever tooling or technology you like. Or simply utilise it to search for infrastructure for indicators of attacks as part of your investigations.
Fully flexible API
Protect your own services and customers
AiTM is not just targeting the big identity providers. Financial services, web applications, advertising platforms, online stores, holiday booking… pretty much anything web based can and is being targeted.
Protect your customers by preventing AiTM infrastructure from accessing your users accounts
DNS is where it all starts
So block it there
Ingest our data into your protective DNS service and break the whole AiTM cycle before it even starts.
Extend beyond the endpoint
Cyber security is a team game
Which is why we also make our feeds available to others, enabling them to uplift the services which they provide in a way that wouldn’t otherwise be possible.
Incorporate our unique feeds into your own service offerings.
“It’s going to be a game-changer for cyber security efforts. The proactive detection and blocking of malicious infrastructure before it can be used in attacks is incredibly valuable”
Why AiTM?
The vast majority of successful attacks that Lab539 observe relate to account compromise. Most now also bypass multi factor authentication controls such as Microsoft Authenticator.
To mitigate these attacks we created some rather clever (and we believe unique) capability to detect and block the infrastructure which will be used for these attacks before it has even been fully deployed, and usually long before the attacks start.
This is not a feed of IP addresses that have been observed carrying out nefarious activities, this is a feed of infrastructure that is are about to carry out nefarious activities. We proactively detect both front and back end AiTM infrastructure.
AiTM attacks are the direct result of a failure, by major vendors, to properly threat model the systems your organisation rely on at the design stage - the result of building systems resilient to current attacks while ignoring the fact that adversaries adapt.
…AiTM shouldn’t have been a thing. And, yet here we are.
What makes Lab539’s AiTM feed unique?
The vast majority of threat intel feeds are historical references, they relate to attacks which have occurred. We don’t believe that there needs to be victims before defences can be implemented. Which is why we proactively track and hunt down adversaries and share details of their infrastructure in real time. Our goal is to enable you to prevent AiTM, and other attacks, before they even commence.
Our approach to proactive hunting means that the data in our feed is usually days to weeks more current than the major security vendors (obviously excluding any that consume our feed!). In many cases we detect malicious infrastructure that never makes it onto their radars. Modern attacks don’t start with malware.
Our goal is also to make our threat intelligence as easy to consume as possible, and provide you access to the raw data, because your defences should work for you.
It’s like having an extension of your security team constantly hunting down this infrastructure and feeding it directly into your environment in order to protect your users.